AI-Powered Cybersecurity Software for Threat Detection
AI-Powered Cybersecurity Software for Threat Detection
AI-Powered Cybersecurity Software for Threat Detection
Industry
Industry
Industry
Cybersecurity
Cybersecurity
Cybersecurity
Responsibilities
Responsibilities
Responsibilities
As the sole UX/UI expert, I collaborated with the technical team to structure existing technologies and concepts, define the app’s target users and objectives, and outline its key features and user flow. Additionally, I developed prototypes to refine and validate the user experience.
As the sole UX/UI expert, I collaborated with the technical team to structure existing technologies and concepts, define the app’s target users and objectives, and outline its key features and user flow. Additionally, I developed prototypes to refine and validate the user experience.
As the sole UX/UI expert, I collaborated with the technical team to structure existing technologies and concepts, define the app’s target users and objectives, and outline its key features and user flow. Additionally, I developed prototypes to refine and validate the user experience.

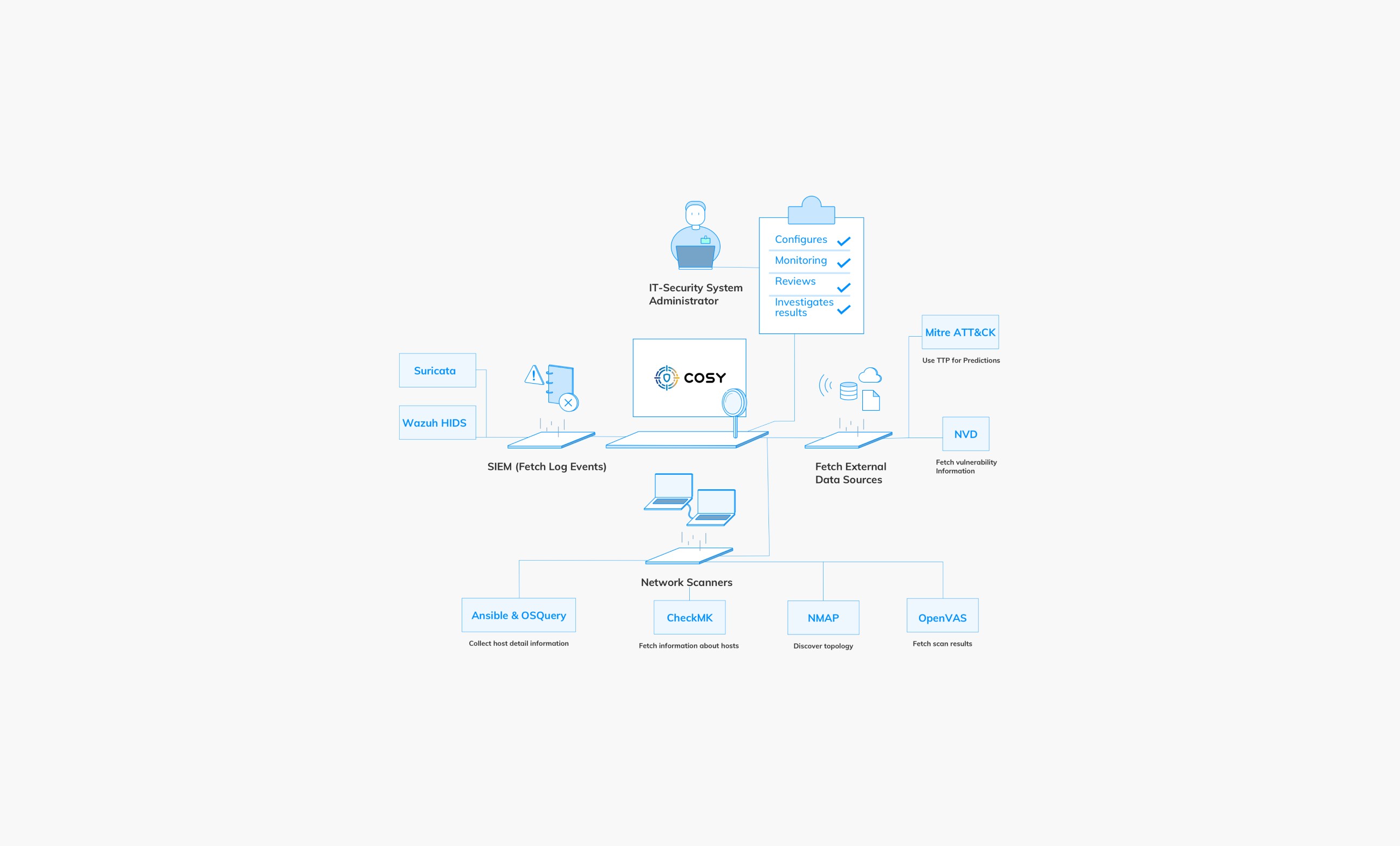
Cosy is a cybersecurity system that leverages a Reinforcement Learning (RL) agent within a simulated environment to identify potential attack paths based on infrastructure scans and detected vulnerabilities. The project is developed for the Bundesamt für Sicherheit in der Informationstechnik (BSI).
Cosy is a cybersecurity system that leverages a Reinforcement Learning (RL) agent within a simulated environment to identify potential attack paths based on infrastructure scans and detected vulnerabilities. The project is developed for the Bundesamt für Sicherheit in der Informationstechnik (BSI).
Cosy is a cybersecurity system that leverages a Reinforcement Learning (RL) agent within a simulated environment to identify potential attack paths based on infrastructure scans and detected vulnerabilities. The project is developed for the Bundesamt für Sicherheit in der Informationstechnik (BSI).
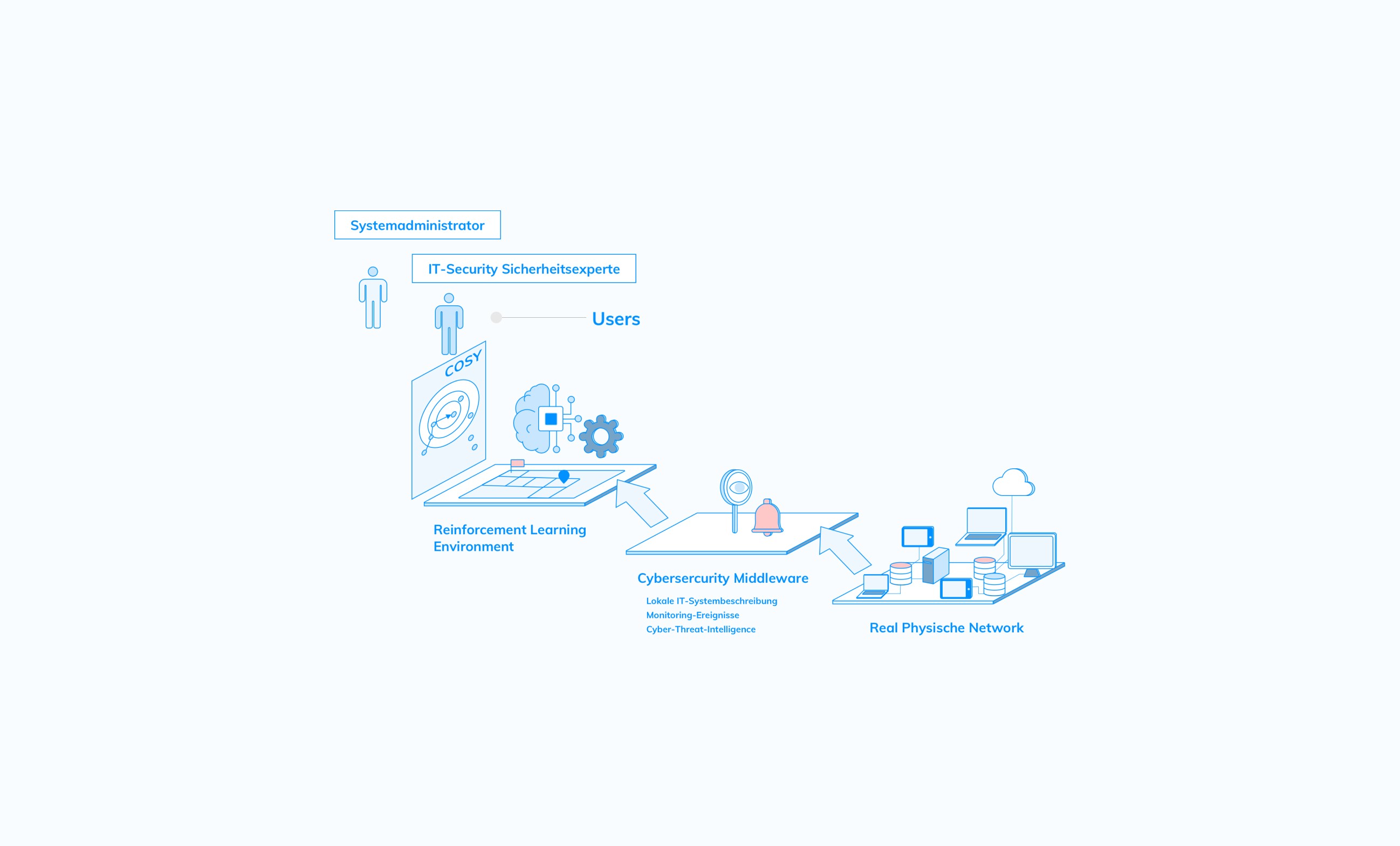

Problem
Problem
Problem
System administrators typically have to manually manage security processes and check for vulnerabilities, a time-consuming task prone to human error.
System administrators typically have to manually manage security processes and check for vulnerabilities, a time-consuming task prone to human error.
System administrators typically have to manually manage security processes and check for vulnerabilities, a time-consuming task prone to human error.
Approach
Approach
Approach
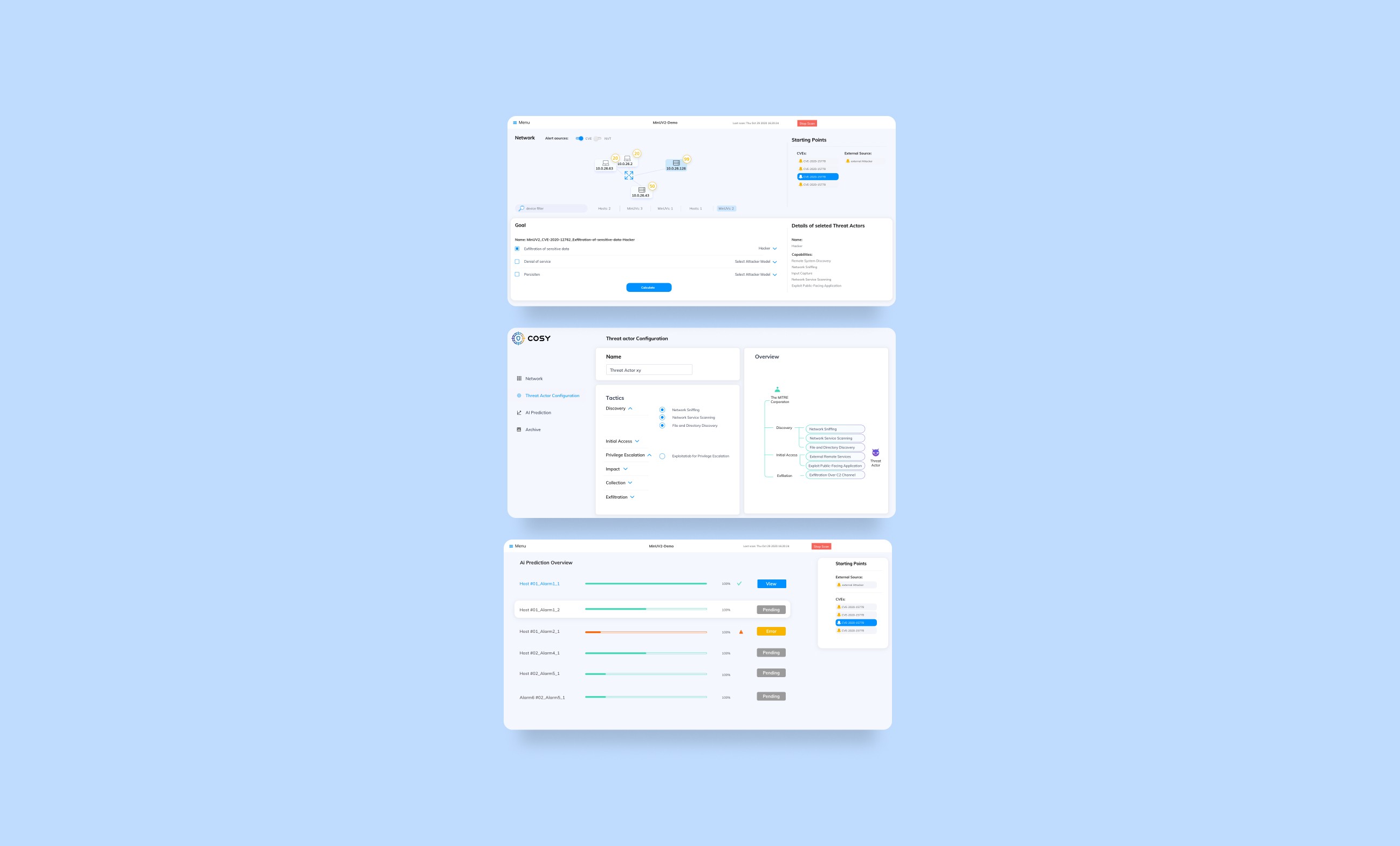
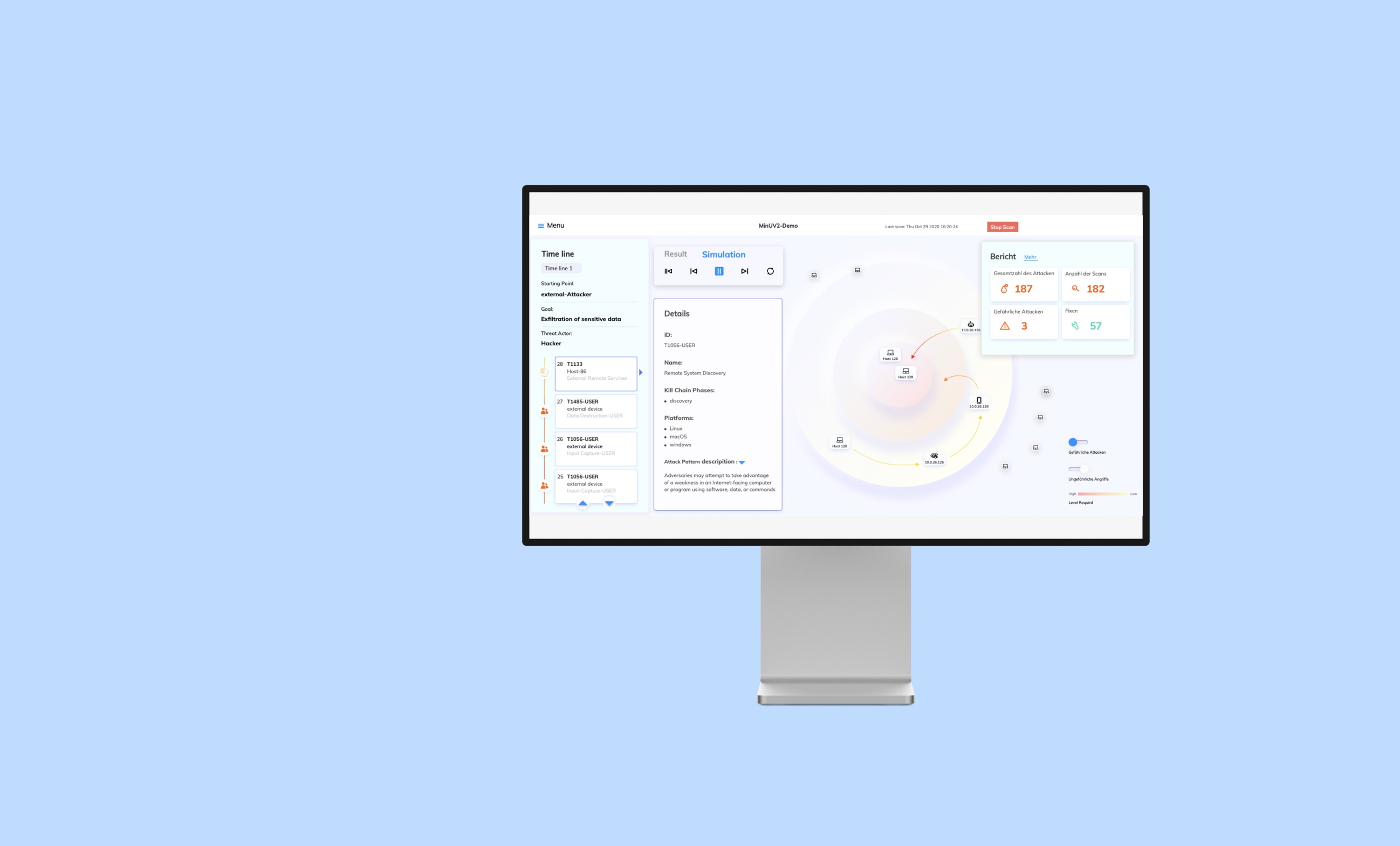
The app provides administrators with a comprehensive overview of the system and its infrastructure. Automated security assessments continuously detect and display new vulnerabilities or alerts. Additionally, administrators can simulate attack scenarios based on detected vulnerabilities to identify potential system weaknesses. These simulations can be initiated manually or triggered by alerts, optimizing efficiency and saving time. The app also offers predictive insights, allowing administrators to review forecasted attack paths and risks.
The app provides administrators with a comprehensive overview of the system and its infrastructure. Automated security assessments continuously detect and display new vulnerabilities or alerts. Additionally, administrators can simulate attack scenarios based on detected vulnerabilities to identify potential system weaknesses. These simulations can be initiated manually or triggered by alerts, optimizing efficiency and saving time. The app also offers predictive insights, allowing administrators to review forecasted attack paths and risks.
The app provides administrators with a comprehensive overview of the system and its infrastructure. Automated security assessments continuously detect and display new vulnerabilities or alerts. Additionally, administrators can simulate attack scenarios based on detected vulnerabilities to identify potential system weaknesses. These simulations can be initiated manually or triggered by alerts, optimizing efficiency and saving time. The app also offers predictive insights, allowing administrators to review forecasted attack paths and risks.
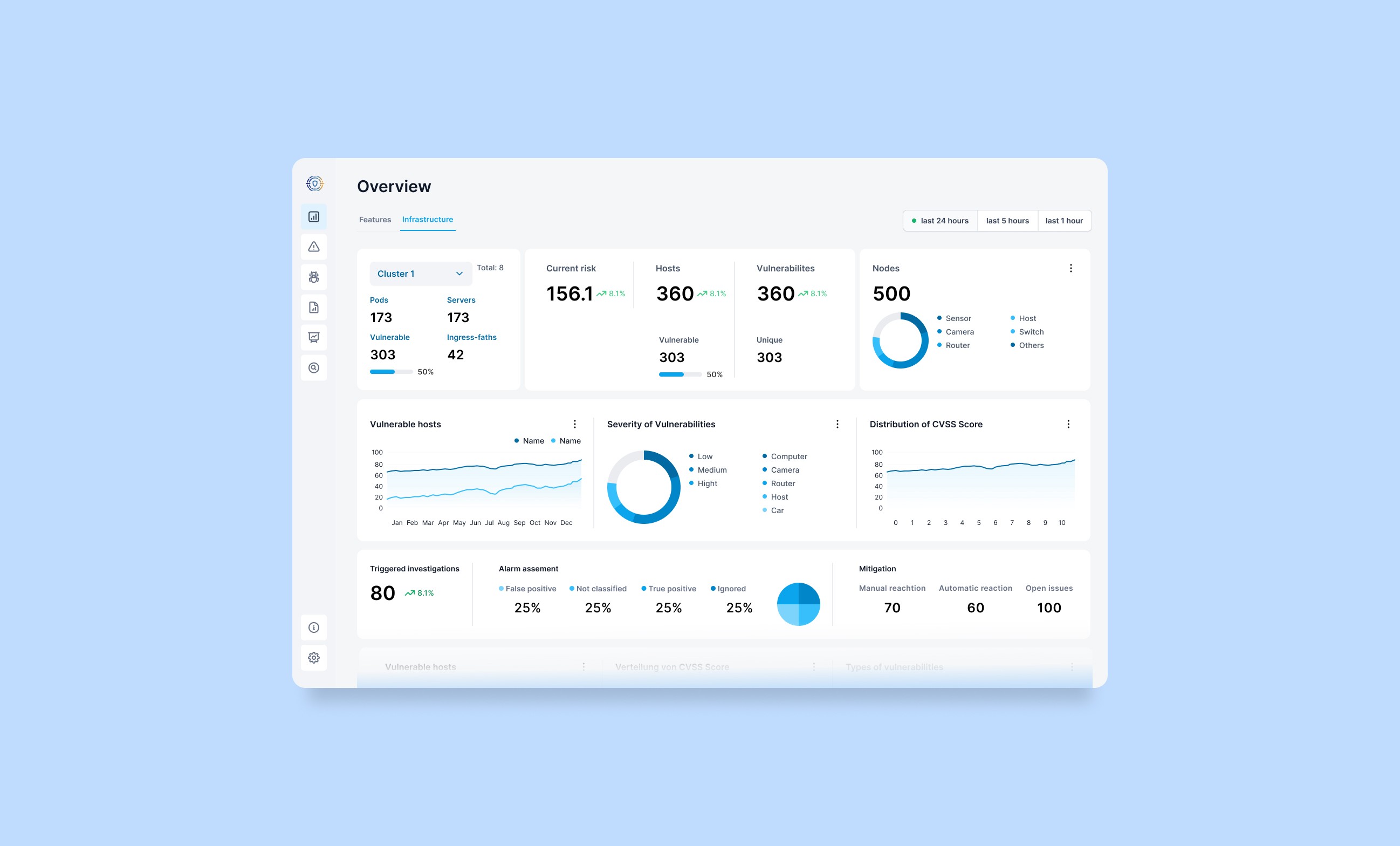

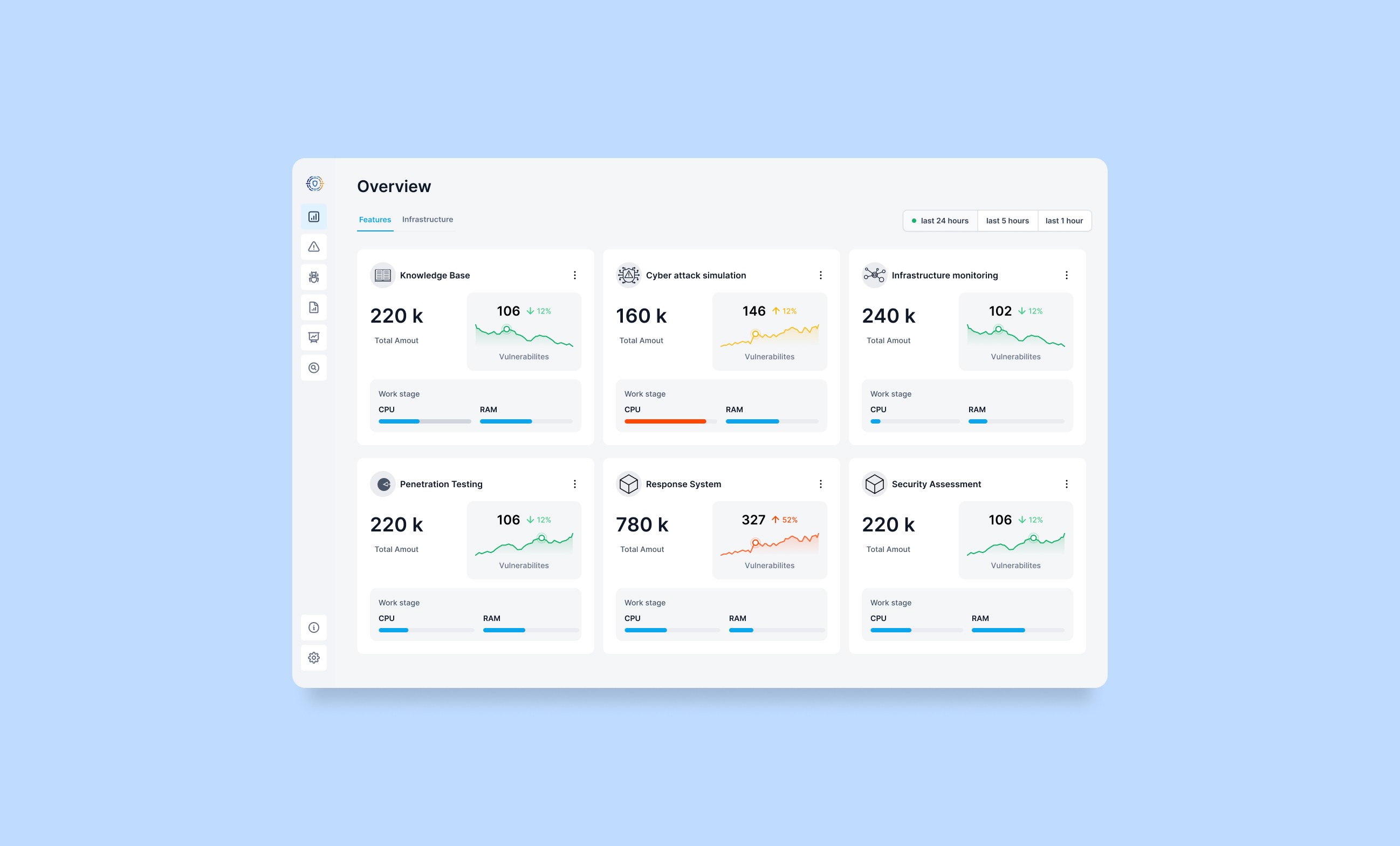

Challenges
Challenges
Challenges
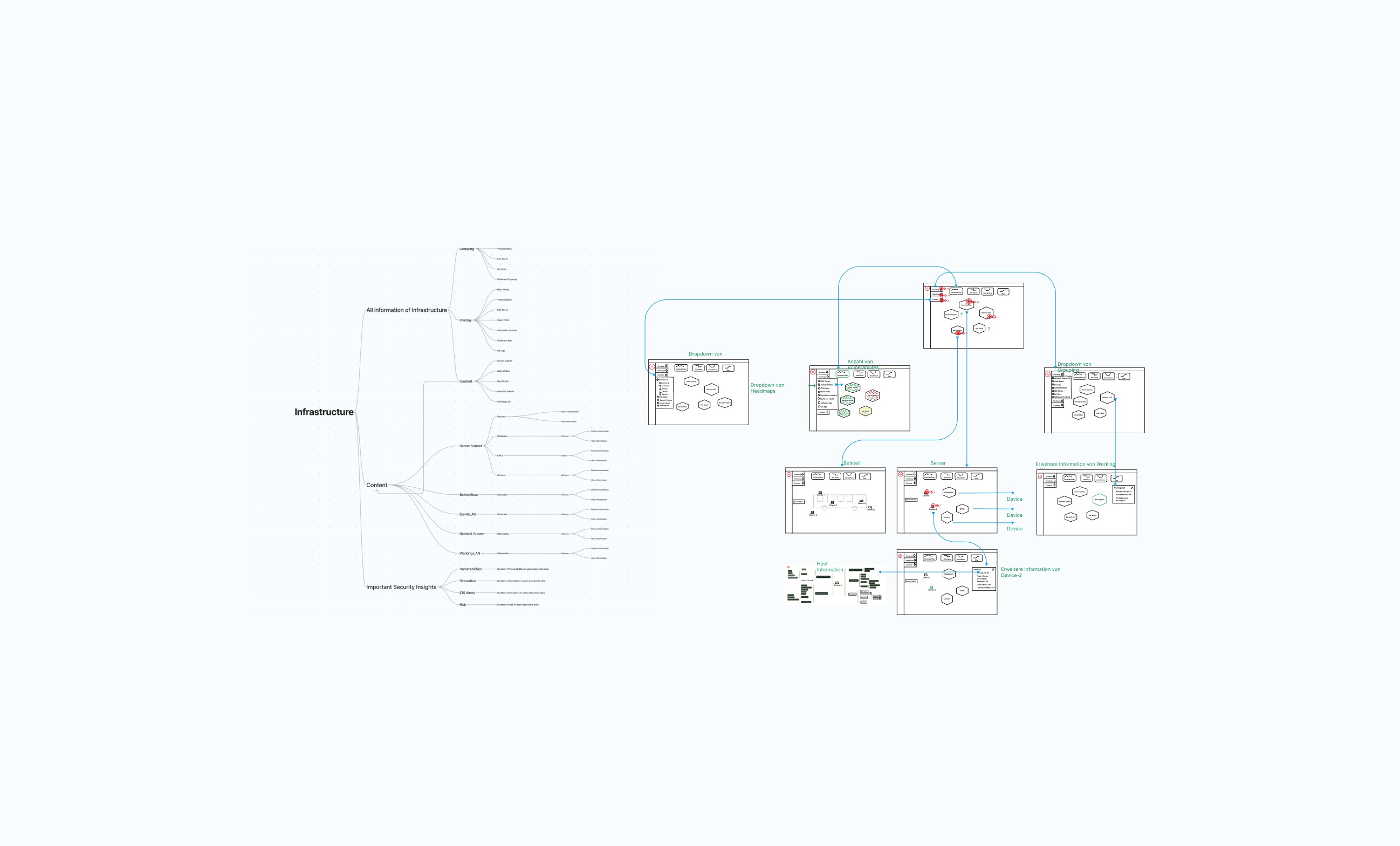
This project is highly technology-driven and operates within a highly specialized field. One of the key challenges was developing an application with a purely technical team that had little experience in app development. As the UX/UI expert, I needed to quickly learn and understand new technologies and concepts from the tech team while translating their semi-abstract ideas and data into a functional and user-friendly application.
This project is highly technology-driven and operates within a highly specialized field. One of the key challenges was developing an application with a purely technical team that had little experience in app development. As the UX/UI expert, I needed to quickly learn and understand new technologies and concepts from the tech team while translating their semi-abstract ideas and data into a functional and user-friendly application.
This project is highly technology-driven and operates within a highly specialized field. One of the key challenges was developing an application with a purely technical team that had little experience in app development. As the UX/UI expert, I needed to quickly learn and understand new technologies and concepts from the tech team while translating their semi-abstract ideas and data into a functional and user-friendly application.